Loading ...
Loading ...
Loading ...
105
This chapter explains how to perform F-code communication operations. F-code communication is possible with
machines of other manufacturers that also support F-code communication.
F-CODE COMMUNICATION
Exchange of confidential documents (confidential communication), retrieval (polling) and distribution (polling memory) of
information, distribution of information to multiple destinations (relay broadcast transmission) are possible with other
machines that support F-code communication.
An F-code* is specified in each communication, enabling a higher level of security.
* F-code is a communication function based on the G3 standard of the ITU-T.
HOW F-CODES WORK
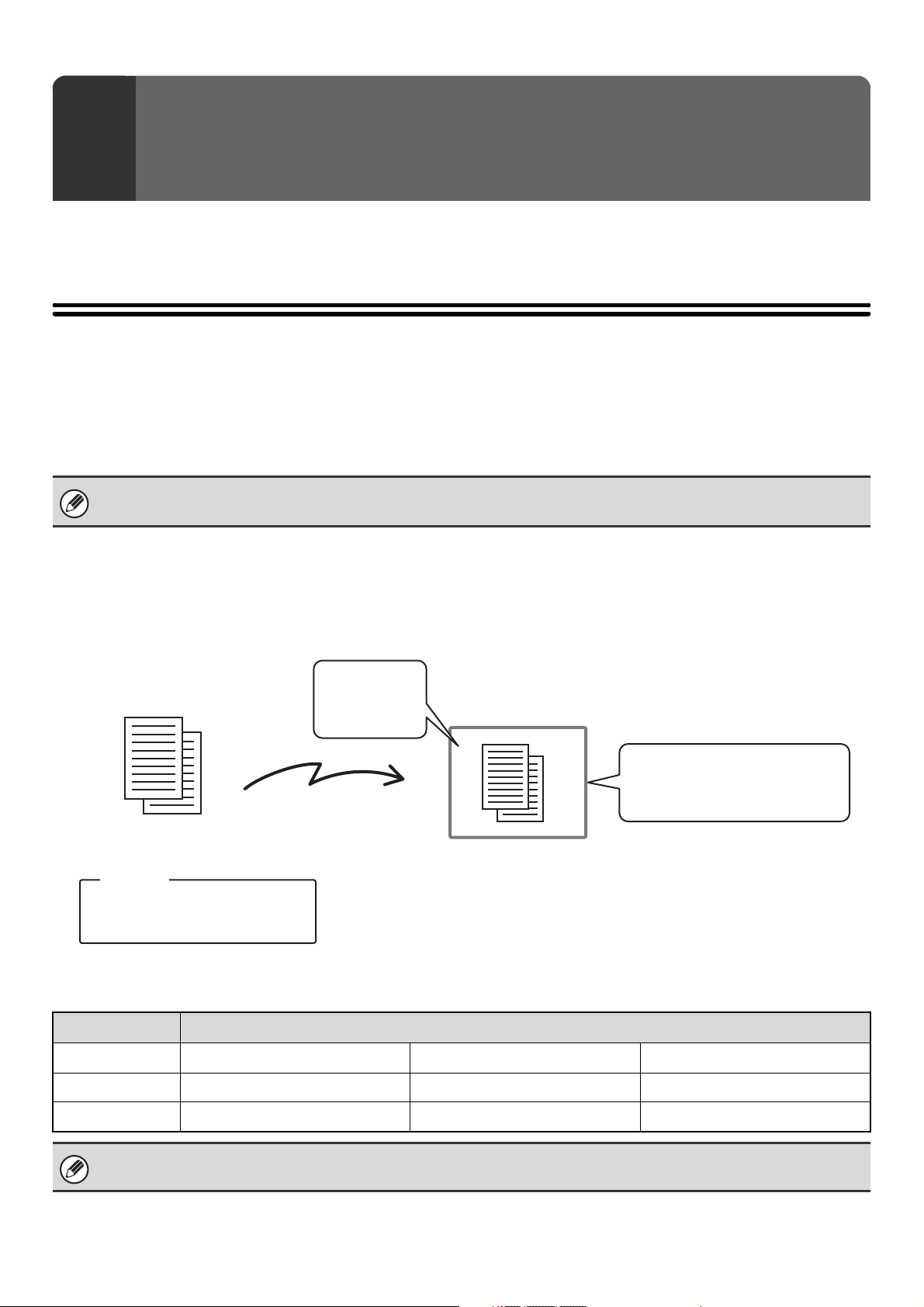
A fax that is transmitted with an F-code is received to the memory box in the receiving machine specified by the F-code
(sub-address and passcode). If the F-code sent by the transmitting machine does not match the F-code in the receiving
machine, reception will not take place.
The products of other manufacturers may use different terms for "sub-address" and "passcode". If you need to contact
the operator of another machine regarding sub-addresses and passcodes, refer to the terms in the table below which
are used by the ITU-T.
8
PERFORMING F-CODE
COMMUNICATION
The ITU-T is a United Nations organization that establishes communications standards. It is a department of the International
Telecommunication Union (ITU), which coordinates global telecommunications networks and services.
Your machine ITU-T
F-code polling memory box F-code confidential box
F-code relay broadcast memory box
Sub-address SEP SUB SUB
Passcode PWD SID SID
An F-code consists of a sub-address and passcode, and cannot be longer than 20 digits.
Reception to
memory box
specified by
the F-code
Fax number of other
machine
+
F-code
Sub-address: AAAAAAAA
Passcode: XXXXXXXX
Box name: BBBB
Sub-address: AAAAAAAA
Passcode: XXXXXXXX
Memory box for
F-code
communication
Loading ...
Loading ...
Loading ...