Loading ...
Loading ...
Loading ...
4.4.4 SSH Config
As stipulated by IETF (Internet Engineering Task Force), SSH (Secure Shell) is a security
protocol established on application and transport layers. SSH-encrypted-connection is similar
to a telnet connection, but essentially the old telnet remote management method is not safe,
because the password and data transmitted with plain-text can be easily intercepted. SSH can
provide information security and powerful authentication when you log on to the switch
remotely through an insecure network environment. It can encrypt all the transmission data and
prevent the information in a remote management being leaked.
Comprising server and client, SSH has two versions, V1 and V2 which are not compatible with
each other. In the communication, SSH server and client can auto-negotiate the SSH version
and the encryption algorithm. After getting a successful negotiation, the client sends
authentication request to the server for login, and then the two can communicate with each
other after successful authentication. This switch supports SSH server and you can log on to
the switch via SSH connection using SSH client software.
SSH key can be downloaded into the switch. If the key is successfully downloaded, the
certificate authentication will be preferred for SSH access to the switch.
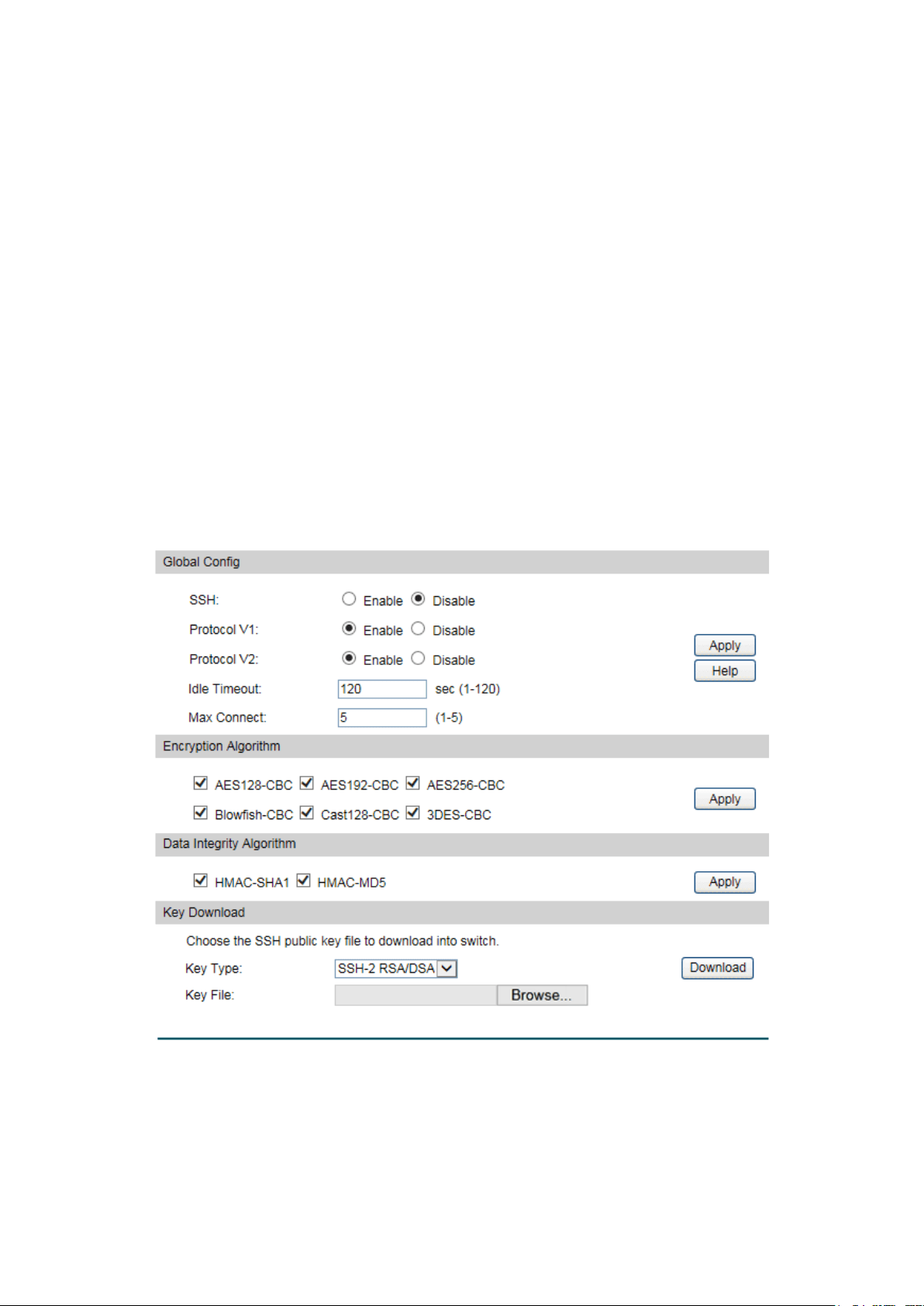
Choose the menu System→Access Security→SSH Config to load the following page.
Figure 4-19 SSH Config
The following entries are displayed on this screen
:
Global Config
SSH:
Select Enable/Disable SSH function.
33
Loading ...
Loading ...
Loading ...