Loading ...
Loading ...
Loading ...
12.6.6 Authentication Method List Config
Before you configure AAA authentication on a certain application, you should define an
authentication method list first. An authentication method list describes the sequence and
authentication method to be queried to authenticate a user.
The switch uses the first method listed to authenticate users, if that method fails to respond,
the switch selects the next authentication method in the method list. This process continues
until there is a successful communication with a listed authentication method or until all defined
methods are exhausted. If authentication fails at any point in this circle, which means the
secure server or the local switch denies the user’s access, the authentication process stops
and no other authentication methods are attempted.
For example, if a user defines an authentication login method list as tacacs-radius-local, the
switch will send an authentication request to the fist TACACS+ server in the tacacs server
group. If there is no response, the switch will send an authentication request to the second
TACACS+ server in the tacacs server group and so on, until the tacacs server group list is
exhausted. Then the RADIUS server group will be queried. If no authentication is accomplished
in the RADIUS server list, the switch will authenticate the user locally. This forms a backup
system for authentication.
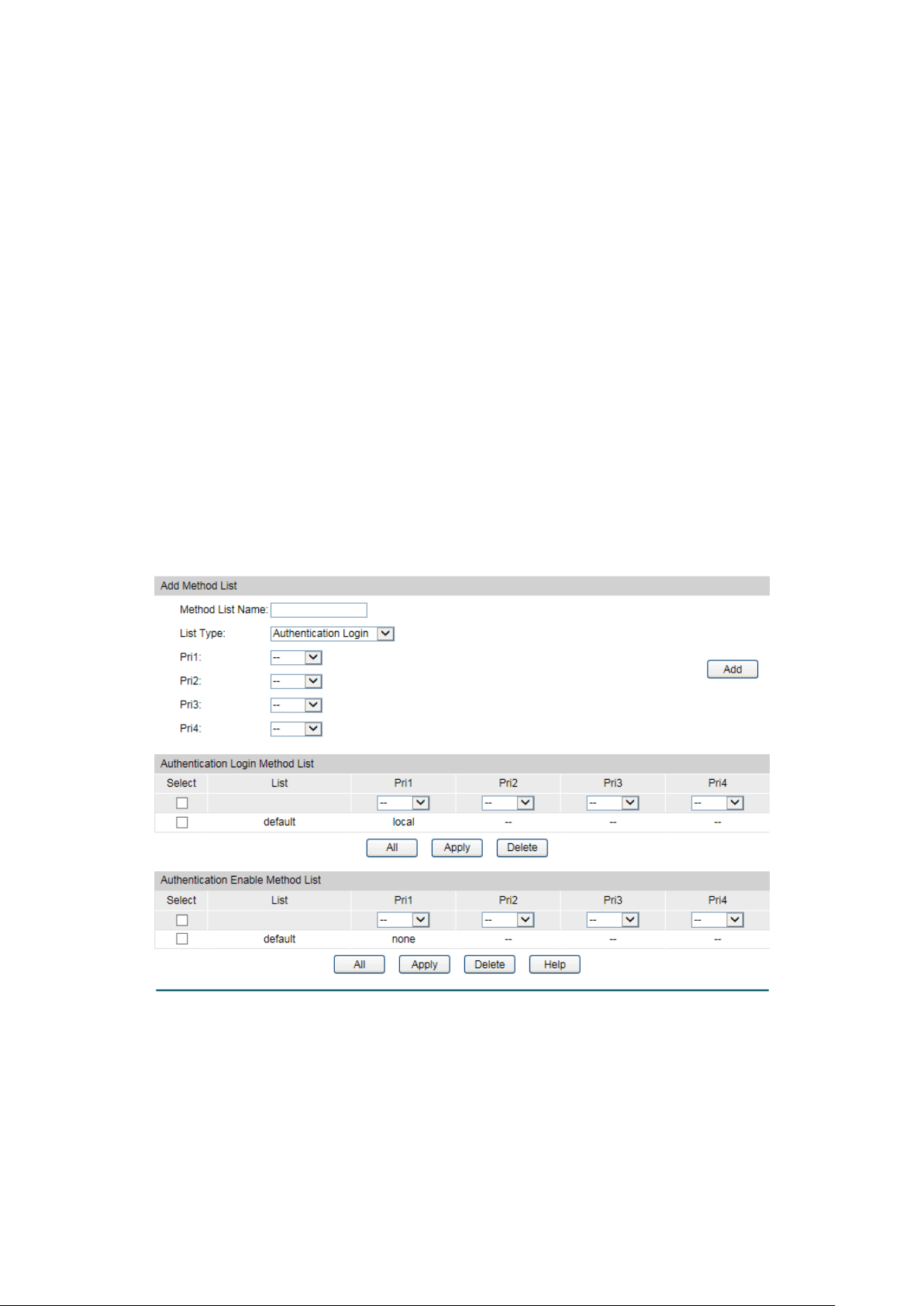
Choose the menu Network Security→AAA→Method List to load the following page.
Figure 12-30 Authentication Method List Config
Configuration Procedure
1) Enter the method list name.
2) Specify the authentication type as Login or Enable.
3) Configure the authencation method with priorities. The options are radius, tacacs, local or
user-defined server groups.
181
Loading ...
Loading ...
Loading ...