Loading ...
Loading ...
Loading ...
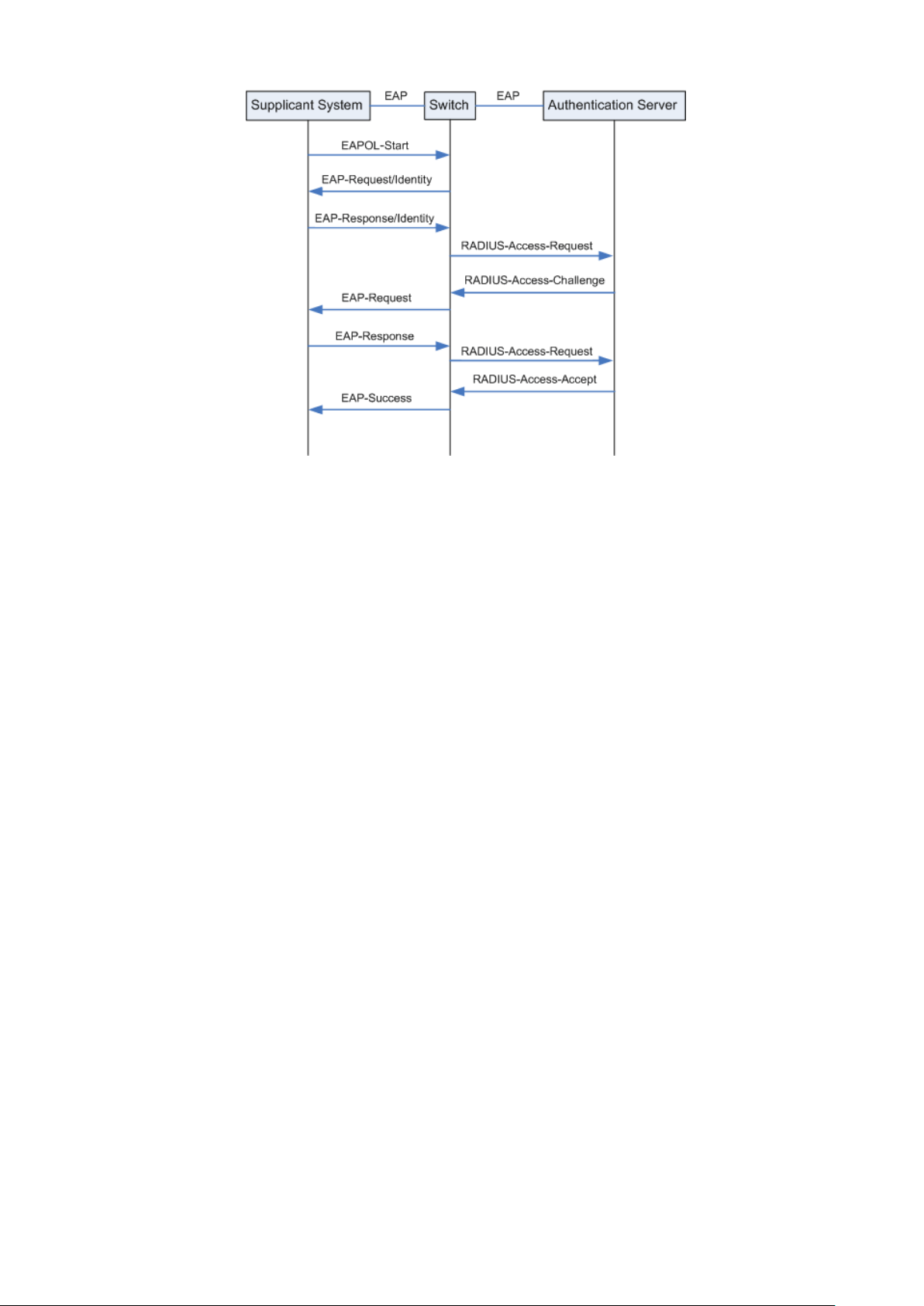
Figure 12-20 EAP-MD5 Authentication Procedure
(1) A supplicant system launches an 802.1X client program via its registered user name and
password to initiate an access request through the sending of an EAPOL-Start packet to
the switch. The 802.1X client program then forwards the packet to the switch to start the
authentication process.
(2) Upon receiving the authentication request packet, the switch sends an
EAP-Request/Identity packet to ask the 802.1X client program for the user name.
(3) The 802.1X client program responds by sending an EAP-Response/Identity packet to the
switch with the user name included. The switch then encapsulates the packet in a RADIUS
Access-Request packet and forwards it to the RADIUS server.
(4) Upon receiving the user name from the switch, the RADIUS server retrieves the user name,
finds the corresponding password by matching the user name in its database, encrypts the
password using a randomly-generated key, and sends the key to the switch through an
RADIUS Access-Challenge packet. The switch then sends the key to the 802.1X client
program.
(5) Upon receiving the key (encapsulated in an EAP-Request/MD5 Challenge packet) from the
switch, the client program encrypts the password of the supplicant system with the key
and sends the encrypted password (contained in an EAP-Response/MD5 Challenge packet)
to the RADIUS server through the switch. (The encryption is irreversible.)
(6) The RADIUS server compares the received encrypted password (contained in a RADIUS
Access-Request packet) with the locally-encrypted password. If the two match, it will then
send feedbacks (through a RADIUS Access-Accept packet and an EAP-Success packet) to
the switch to indicate that the supplicant system is authorized.
(7) The switch changes the state of the corresponding port to accepted state to allow the
supplicant system access the network. And then the switch will monitor the status of
supplicant by sending hand-shake packets periodically. By default, the switch will force the
supplicant to log off if it cannot get the response from the supplicant for two times.
170
Loading ...
Loading ...
Loading ...