Loading ...
Loading ...
Loading ...
Administrator can be acquainted with the location of the DHCP Client via Option 82 so as to
locate the DHCP Client for fulfilling the security control and account management of Client. The
Server supported Option 82 also can set the distribution policy of IP addresses and the other
parameters according to the Option 82, providing more flexible address distribution way.
Option 82 can contain 255 sub-options at most. If Option 82 is defined, at least a sub-option
should be defined. This switch supports two sub-options: Circuit ID and Remote ID. Since there
is no universal standard about the content of Option 82, different manufacturers define the
sub-options of Option 82 to their need. For this switch, the sub-options are defined as the
following: The Circuit ID is defined to be the number of the port which receives the DHCP
Request packets and its VLAN number. The Remote ID is defined to be the MAC address of
DHCP Snooping device which receives the DHCP Request packets from DHCP Clients.
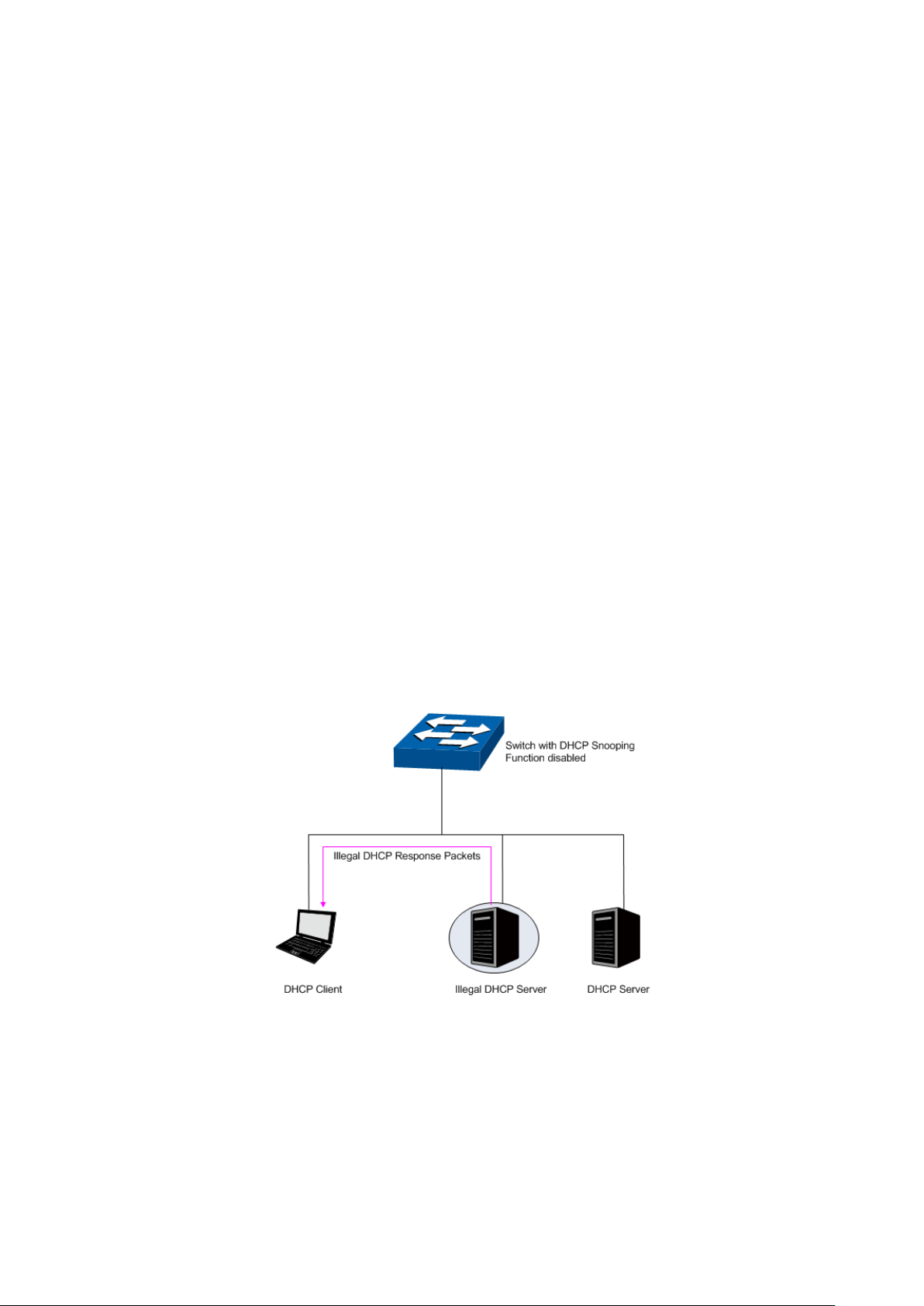
DHCP Cheating Attack
During the working process of DHCP, generally there is no authentication mechanism between
Server and Client. If there are several DHCP servers in the network, network confusion and
security problem will happen. The common cases incurring the illegal DHCP servers are the
following two:
(1) It’s common that the illegal DHCP server is manually configured by the user by mistake.
(2) Hacker exhausted the IP addresses of the normal DHCP server and then pretended to
be a legal DHCP server to assign the IP addresses and the other parameters to Clients.
For example, hacker used the pretended DHCP server to assign a modified DNS server
address to users so as to induce the users to the evil financial website or electronic
trading website and cheat the users of their accounts and passwords. The following
figure illustrates the DHCP Cheating Attack implementation procedure.
Figure 12-7 DHCP Cheating Attack Implementation Procedure
DHCP Snooping feature only allows the port connected to the DHCP Server as the trusted port
to forward all types of DHCP packets and thereby ensures that users get proper IP addresses.
DHCP Snooping is to monitor the process of the Host obtaining the IP address from DHCP
server, and record the IP address, MAC address, VLAN and the connected Port number of the
Host for automatic binding. The bound entry can cooperate with the ARP Inspection, IP Source
Guard and the other security protection features. DHCP Snooping feature prevents the
155
Loading ...
Loading ...
Loading ...