Loading ...
Loading ...
Loading ...
Conguring IEEE 802.1X Authentication Settings
3JX3-07E
The machine can connect to an 802.1X network as a client de
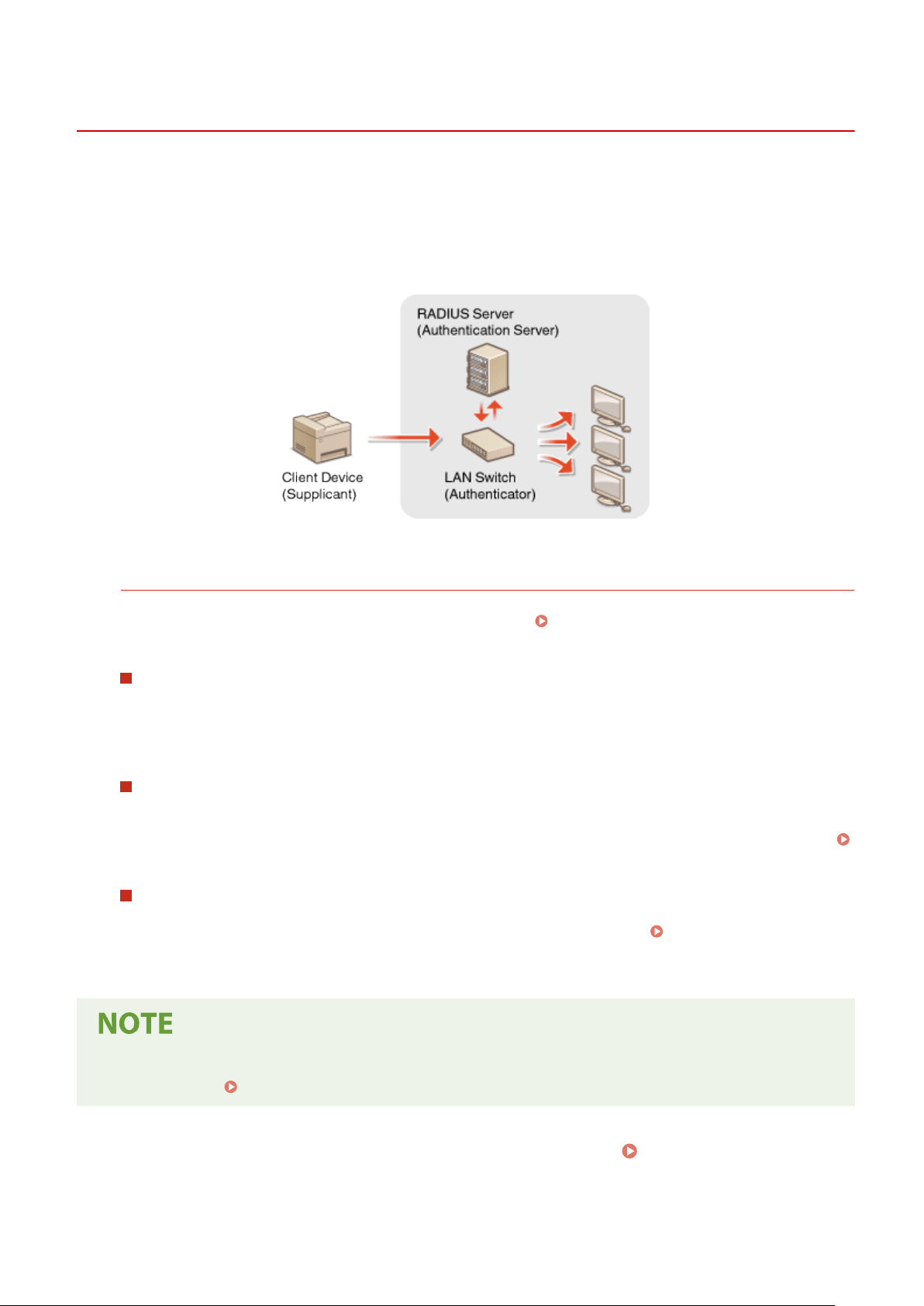
vice. A typical 802.1X network consists of a RADIUS server
(authentication server), LAN switch (authenticator), and client devices with authentication software (supplicants). If a
device tries to connect to the 802.1X network, the device must go through user authentication in order to prove that
the connection is made by an authorized user. Authentication information is sent to and checked by a RADIUS server,
which permits or rejects communication to the network depending on the authentication result. If authentication fails,
a LAN switch (or an access point) blocks access from the outside of the network.
IEEE 802.1X Authentication Method
Select the authentication method from the options below. If necessary, install or register a key and certicate or
a CA certicate befor
e conguring IEEE 802.1X authentication (
Registering the Key and Certicate for
Network Communication
(P. 387) ).
TLS
The machine and the authentication server authenticate each other b
y mutually verifying their certicates. A
key and certicate issued by a certication authority (CA) is required for the client authentication (when
authenticating the machine). For the server authentication, a CA certicate installed via the Remote UI can be
used in addition to a CA certicate preinstalled in the machine.
TTLS
This authentication method uses a user name and passwor
d for the client authentication and a CA certicate
for the server authentication. MSCHAPv2 or PAP can be selected as the internal protocol. TTLS can be used
with PEAP at the same time. Enable TLS for the Remote UI before conguring this authentication method (
Conguring the Ke
y and Certicate for TLS(P. 378) ).
PEAP
The r
equired settings are almost the same as those of TTLS. MSCHAPv2 is used as the internal protocol.
Enable TLS for the Remote UI before conguring this authentication method (
Conguring the Ke
y and
Certicate for TLS(P. 378) ).
● For mor
e information about the basic operations to be performed when setting the machine from the
Remote UI, see
Setting Up Menu Options from Remote UI(P. 427) .
1
Start the Remote UI and log in to System Manager Mode. Starting Remote
UI(P
. 417)
Managing the Machine
396
Loading ...
Loading ...
Loading ...