Loading ...
Loading ...
Loading ...
49
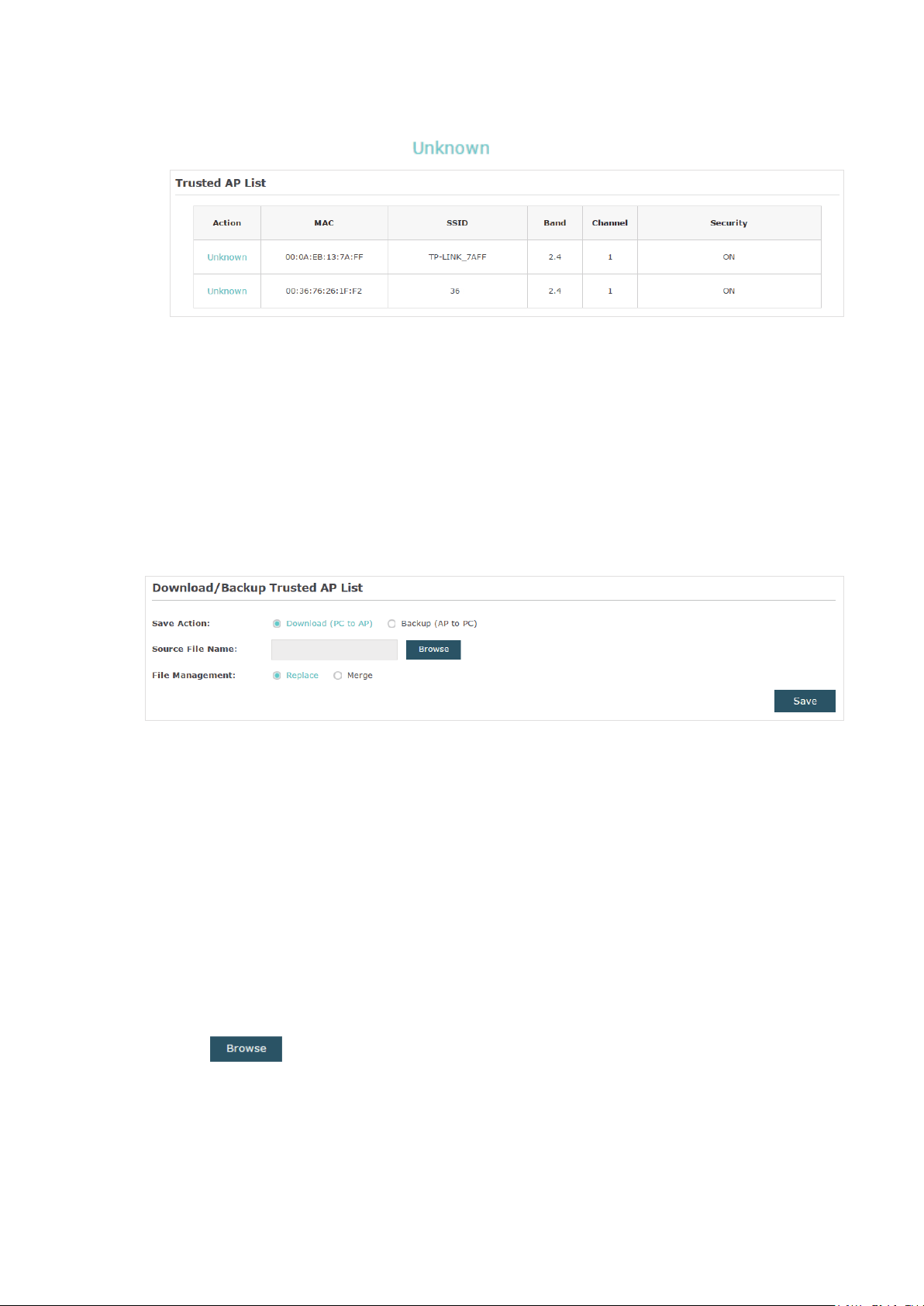
5. View the trusted APs in the Trusted AP List section. To move the specific AP back to
the Rogue AP list, you can click
in the Action column.
Manage the Trusted AP List
You can download the trusted AP list from your local host to the EAP or backup the current
Trusted AP list to your local host.
·
Download the Trusted AP List From the Host
You can import a trusted AP list which records the MAC addresses of the trusted APs. The
AP whose MAC address is in the list will not be detected as a rogue AP.
Follow the steps below to import a trusted AP list to the EAP:
1. Acquire the trusted AP list. There are two ways:
• Backup the list from a EAP. For details, refer to
Backup the Trusted AP List to the
Host
.
• Manually create a trusted AP list. Create a txt. file, input the MAC addresses of the
trusted APs in the format XX:XX:XX:XX:XX:XX and use the Space key to separate each
MAC address. Save the file as a cfg file.
2. On this page, check the box to choose Download (PC to AP).
3. Click
and select the trusted AP list from your local host.
4. Select the file management mode. Two modes are available: Replace and Merge.
Replace means that the current trusted AP list will be replaced by the one you import.
Merge means that the APs in the imported list will be added to the current list with the
original APs remained.
Loading ...
Loading ...
Loading ...