Loading ...
Loading ...
Loading ...
4 Configuration DES-1210/ME Series Metro Ethernet Managed Switch User Manual
8
8
5
5
Figure 4.134 – Security > Smart Binding > Black List
By giving conditions, desired devices information can be screened out below then click Find to search for a
list of the entry:
VID: Enter the VLAN ID number of the device.
IP Address: Enter the IP Address of the device.
MAC Address: Enter the MAC Address of the device.
Port: Enter the port number which the device connects.
Check a box of Delete column to release an entry from the forbidden list then click Apply to delete an entry
from the list.
Click Select All to select all entries, or click Clean to select none of the entries.
Security > Smart Binding > DHCP Snooping List
The DHCP Snooping List page shows the DHCP Snooping list.
Figure 4.135 – Security > Smart Binding > DHCP Snooping List
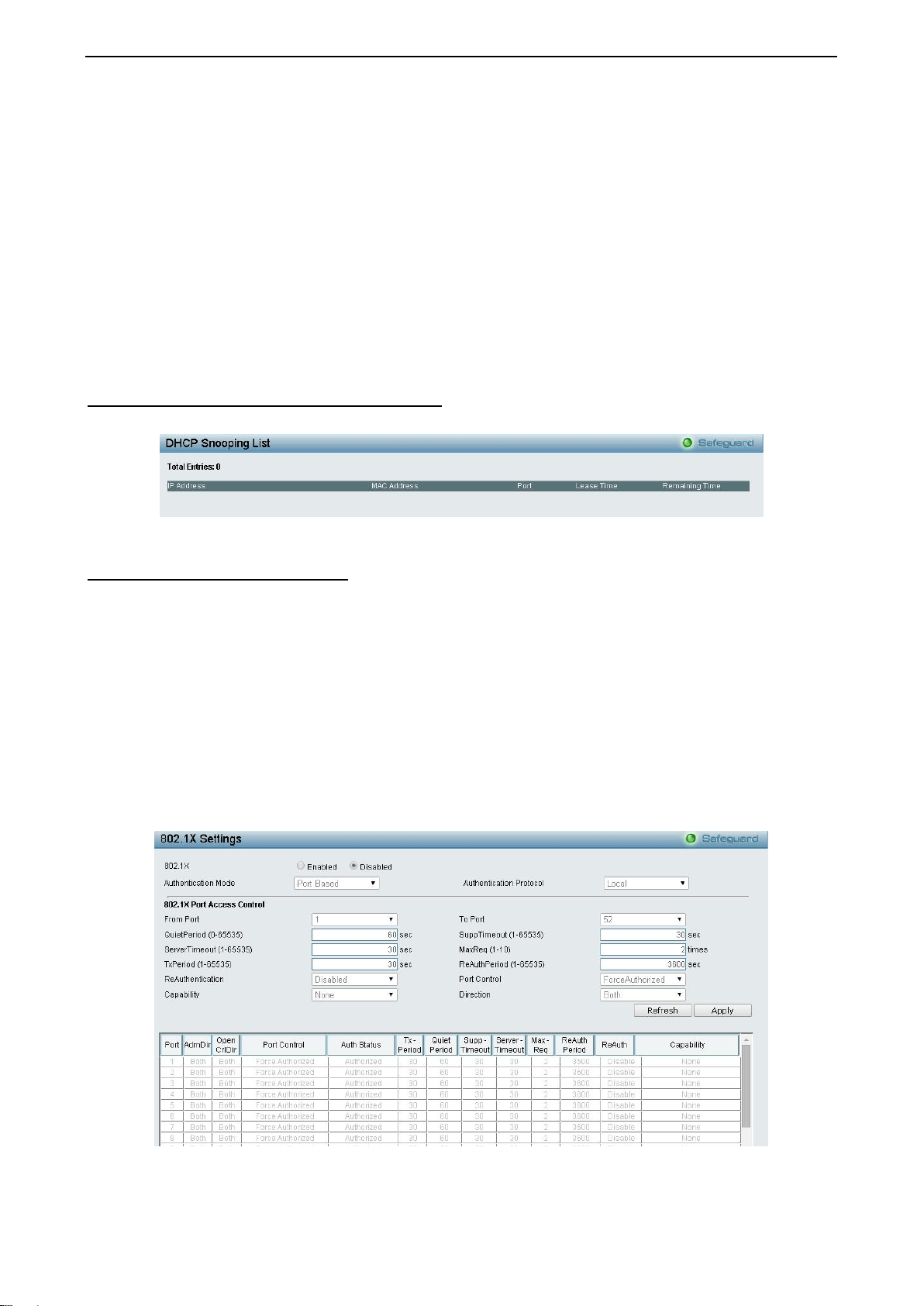
Security > 802.1X > 802.1X Settings
Network switches provide easy and open access to resources by simply attaching a client PC. Unfortunately
this automatic configuration also allows unauthorized personnel to easily intrude and possibly gain access to
sensitive data.
IEEE-802.1X provides a security standard for network access control, especially in Wi-Fi wireless networks.
802.1X holds a network port disconnected until authentication is completed. The switch uses Extensible
Authentication Protocol over LANs (EAPOL) to exchange authentication protocol client identity (such as a
user name) with the client, and forward it to another remote RADIUS authentication server to verify access
rights. The EAP packet from the RADIUS server also contains the authentication method to be used. The
client can reject the authentication method and request another, depending on the configuration of the client
software and the RADIUS server. Depending on the authenticated results, the port is either made available
to the user, or the user is denied access to the network.
The RADIUS servers make the network a lot easier to manage for the administrator by gathering and storing
the user lists.
Figure 4.136 - Security > 802.1X > 802.1X Settings
Loading ...
Loading ...
Loading ...